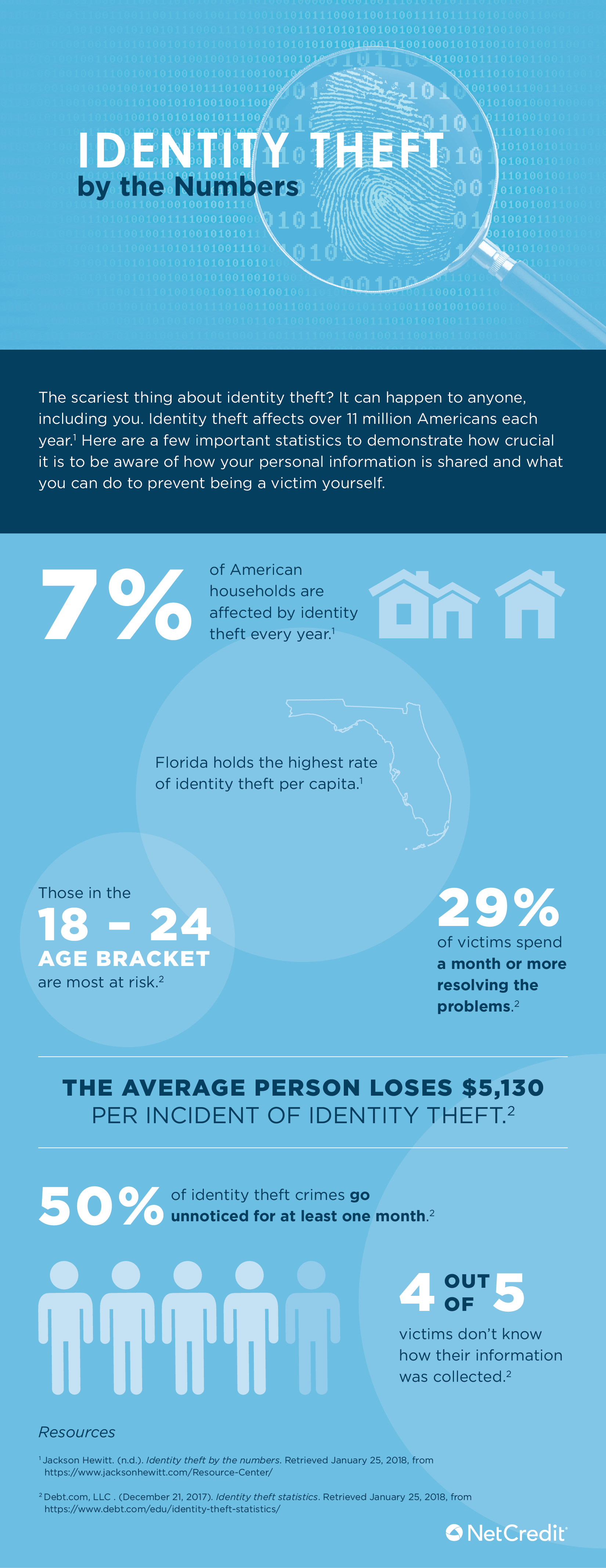
One of the fastest growing crimes in our technology-filled world is the crime of identity theft and the resulting credit fraud. In 2016, identify-theft-related fraud cost consumers over $744 million.1
Identity theft can take many different forms, and different types of personal information can become compromised. For example, many identity thieves typically look to illegally gather personally identifying information, such as legal name, address, social security number, date of birth and account numbers. From this information, thieves can then assume people’s identities and apply for loans, credit cards and even conduct transactions, all without the true owners being aware of the situation. Identity theft complaints were the third most reported to the Federal Trade Commission (FTC) and increased by more than 47% from 2013 to 2015.1
How Identity Thieves Find Your Information
Identity thieves employ a number of different methods to obtain the personal identification information they need to commit fraud, including the following:
- Phishing
Although email filters have gotten better at spotting these scam emails, occasionally consumers still see emails that purport to be from a legitimate source, asking the consumer to supposedly verify personal records. - Hacking
The most publicized cases tend to be of internet hackers who break into the databases of businesses, organizations and government institutions and illegally download personal information. - Dumpster Diving
Other thieves get really dirty by going through the trash of businesses and consumers in search of personal data that should have been shredded. - Spyware
These malware and virus programs record keystrokes and financial information that are then sent to the identity thieves via the web.
How to Protect Yourself Against Identity Theft
One of the ways that consumers can protect their identities is by simply being alert for suspicious activity on their accounts, unwanted calls or inquiries about their credit. Thieves depend on consumer complacency to succeed. Just as burglars are always looking for unlocked windows, identity thieves are looking for individuals who fail to properly secure documents that contain their personal information or do not take precautions with their credit.
An effective strategy for consumers looking to protect themselves is to simply be warier whenever someone asks for personal information. Some institutions have legitimate reasons to ask for your personal information but many don’t need it.
Below are online resources that can help consumers avoid becoming the victims of identity theft and credit fraud:
What Is Identity theft?
- Identity theft and Identity Fraud — Informative page from the Department of Justice explaining what ID theft is.
- Social Security Number — Information from the Social Security Administration with help on what to do if you believe your number is stolen.
- NY Times Information — Helpful collection of information on various parts of Identity theft.
Types of Identity Theft
- Identity Theft Types — Information on the different types of both online and offline theft.
- Types of Theft — Informative page which lists the various types of ID Theft.
Detecting Identity Theft
- Theft Detection — FTC page which provides consumers with useful information on detecting Identity theft.
Identity Theft Prevention
- Protect Your Identity — Informative page from the North Carolina Department of Justice providing help in protecting identities.
- Stop Theft — Information on how to stop ID Theft from occurring.
Reporting Identity Theft
- Creating a Report — Helpful page which provides the steps to take to report an identity theft crime.
- Tips for Recovering From Identity Theft — How to report what happened, get a recovery plan and take that plan into action.
- Preventing and Reporting — Resourceful page that lists information on ID Theft prevention and reporting.
- What to Do — Information from the FTC on the warning signs of identity theft and what to do in the event of being a victim.